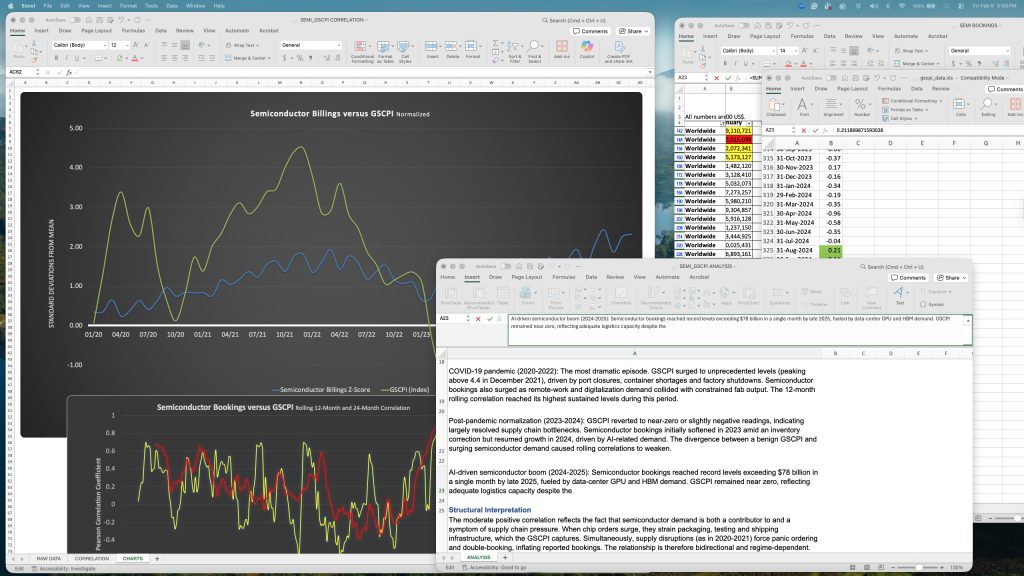
RSAC 2026: Why Every Security Leader Must Attend
Cyber threats are escalating faster than organizations can adapt. Bad actors and ransomware attacks are growing more sophisticated, resulting in significant operational disruption, loss of data and public safety impacts. AI’s growth has only added to the risks organizations face.
The global cost of cybercrime is expected to surge to $13.82 trillion by 2028.
Attending RSAC, happening from March 23-26, can be the difference between making sure your organization’s security stays up-to-date or remains at risk.

What security leaders will take back to their organizations
RSAC is the perfect opportunity to soak up how the industry’s critical thinkers solve some of the world’s biggest security issues.
“The on-floor sessions, in particular, offer direct access to company leaders from notable companies, like Google and IBM, and subject matter experts, giving attendees the rare chance to engage and ask questions,” said Bospar VP, Maddie Coe.
Session topics this year range from the future of the cyber workforce to how Netflix accelerates threat modeling with gen AI to how to secure AI code generation.
RSAC is also a powerful proving ground for startups.
With such a vast and diverse audience, emerging companies have a chance to get their foot in the door, build name recognition and demonstrate how their innovations stack up against industry leaders.
“It’s a massive floor, so the opportunities are endless for startups to meet changemakers, like CISOs and investors, in the space,” said Coe.
The shift everyone will be watching
AI dominated conversations at last year’s RSAC. This year, we’ll see the industry move past the promise of AI and into execution, demonstrating how AI, particularly agentic AI, can be used to make a real impact for security.
“Companies that made claims last year will need to prove the value and results this year,” said Coe.
Additional trends will include cloud security and resiliency and increasingly complex regulatory and compliance standards after a year of heightened geopolitical tension.
Why analyst relations determines who gets heard at RSAC
Thousands of attendees will flood the show floor at RSAC 2026, making standing out among the crowd imperative for tech companies. Analyst relations (AR) will be crucial in doing so.
AR has become a critical lever for tech companies looking to establish their cybersecurity credibility and sharpen their positioning. A good AR program supports these companies in two ways, according to Brandy Patton-Miller, PR and AR manager at Bospar.
AR as a market signal: First, it enables consistent, strategic engagement between vendors and analysts. “A regular cadence of briefings keeps analysts in the know on product roadmaps, M&A activity and go-to-market strategy,” said Patton-Miller.
Combined with formal evaluations, such as Gartner Magic Quadrant or Forrester Wave, this helps analysts build an informed view of the industry and serves as a pre-built shortlist for buyers who need new technology.
AR as strategic intelligence: Second, and something most companies don’t take advantage of, analysts can serve as a powerful feedback loop for vendors. “Analysts see everything in the industry and have likely talked to your competitors,” said Patton-Miller. “They’re uniquely positioned to act as a focus group to test new messaging and strategy.”
Unlike briefings, this isn’t typically earned or free, but the insights can set companies apart from competitors.
Beyond strategy, Patton-Miller notes, leveraging analysts for PR and sales material, such as quotes and commissioned research, can help establish credibility with buyers and media.
Turning RSAC insight into action
RSAC delivers no shortage of insight, but insight alone doesn’t move the industry forward. After four days of sessions, demos and conversations, the real challenge becomes separating signal from noise and translating ideas into action.
On the final day of RSAC 2026 (Thursday, March 26), Bospar will convene a carefully-curated group of cybersecurity vendors, industry analysts and security executives for an invitation-only AR luncheon designed to turn conference insight into strategic clarity.
Featuring leaders from top analyst firms, including Omdia and Frost & Sullivan, the off-the-record forum creates space for candid discussion about what’s real, what’s hype and what security leaders should prioritize next.
“Cybersecurity is built on trust, in data, in authenticated access and in the guidance organizations rely on to make high-stakes decisions,” said Alex Soejarto, SVP of analyst relations at Bospar. “Industry analysts ground their advice in credibility and pattern recognition across the market. By bringing analysts and security leaders together in a focused, unscripted setting, we’re creating the conditions for the kind of dialogue that builds community and drives smarter strategy and stronger outcomes.”
If you’re planning to attend RSAC 2026 and want to sharpen your message, build analyst trust and stand out when it matters most, contact Bospar at results@bospar.com.
Key takeaways:
- RSAC 2026 signals a shift from AI experimentation to execution and proof
- Cloud security, resiliency, agentic AI and regulation will dominate the agenda
- Analyst relations is increasingly critical in a crowded vendor landscape
- RSAC remains a proving ground for credibility, positioning and trust
Cybersecurity in 2026: What CMOs Need to Know
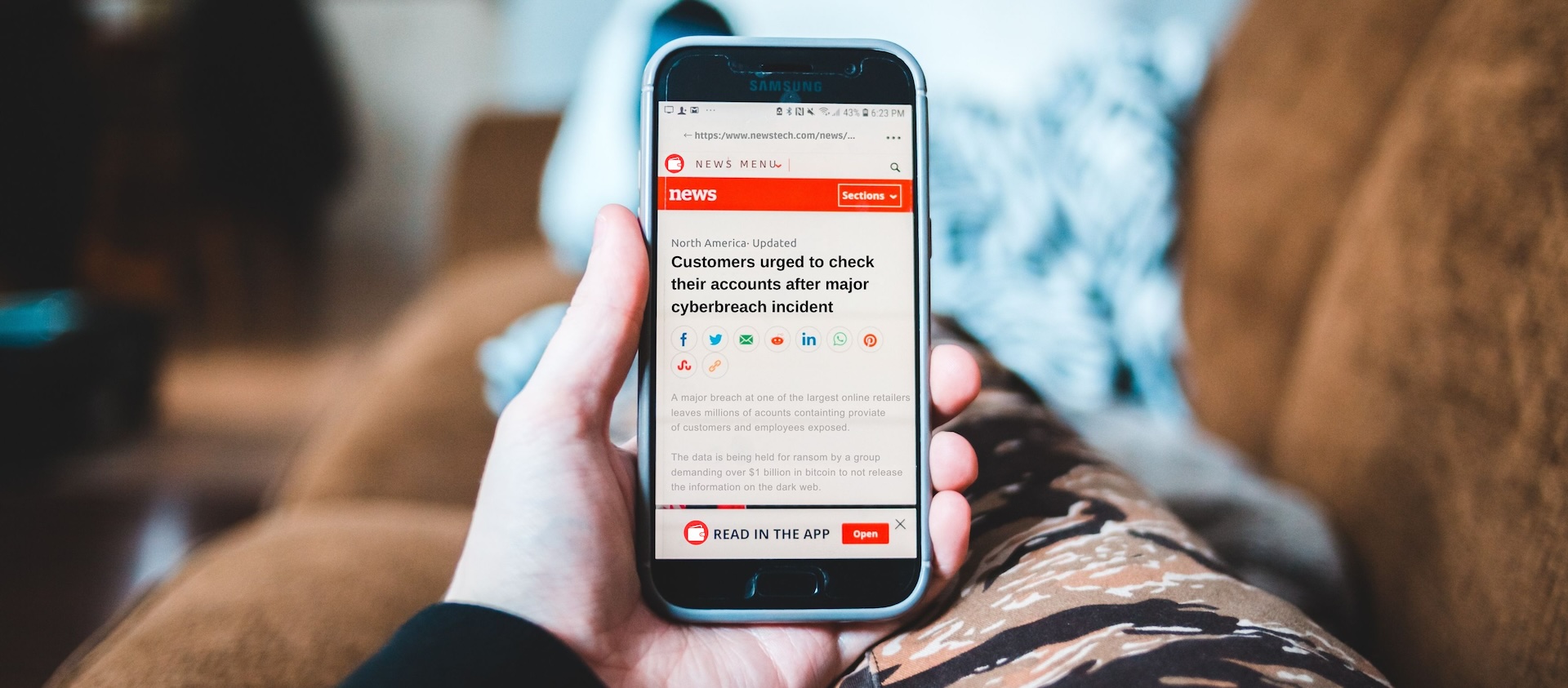
In 2026, cybersecurity is no longer a problem for the CISOs and their team. It’s a brand, customer trust and growth concern, which puts it firmly in the CMO wheelhouse. Cybersecurity risks are now brand risks.
When breaches or damaging deepfakes happen, the story is not just kept within databases and servers, it’s out in the public. It shapes customer perception and can degrade long-term loyalty.
Similar to nearly every business article written in the past two years, the list of what CMOs need to know leads with AI.
AI is supercharging trust-based attacks
Deepfakes, voice cloning and AI-driven impersonations are turning trust into an attack platform. These attacks often won’t look like classic phishing attempts with a suspect-looking bank logo and a poorly-worded email. The new attacks include video calls from a cloned CEO or voicemails from a partner stitched together from videos and other content. Trust is right in CMOs’ wheelhouse, so they should understand how bad actors abuse trust and how the organization is communicating to all stakeholders about successful or thwarted incidents.
Recovery instead of 100% prevention
There’s an emphasis on resilience and recovery over prevention of every threat. Businesses are seeing cybersecurity as part of risk management, not something that can be prevented entirely.
There’s growing board-level awareness of cyber threats, which means it’s not just the job for the CISO, but also the CMO who manages brand and reputational risk. It’s an “if not now, when” strategy that looks at threats realistically, accepting they’ll happen but putting in place both technical safeguards like data segmentation and communications plans to discuss a breach that supports the organization’s broader resilience.
The attack surface is big and growing
Data now lives everywhere: in CRMs, support tools, within AI tools and in integrated platforms from third-party providers. Even if the breach happens within someone else’s platform, customers still see it as the organization’s problem. They don’t care if an outside vendor didn’t have good patch updating procedures and opened up an avenue for an attack. They care that the company that hired this vendor didn’t protect their data and they might have their identity stolen.
CMOs increasingly need visibility into where customer data goes and who touches it. The “it was a third party” response is no longer an acceptable answer with customers who are tired of receiving offers of one year free of credit monitoring in response to data leaks.
Watching your own team
Marketing often holds some of the company’s most valuable data, from customer and prospect lists to partner details and campaign analytics. That information is exactly what attackers want, and it doesn’t take a malicious insider for things to go wrong. One compromised account, a “1234ABCD” password or careless click can turn an ordinary workday into a company-wide crisis.
That’s why marketing teams need to be just as fluent in cybersecurity basics as they are in lead generation. CISOs and CMOs can work together to create role-specific training that focuses on everyday behaviors. They can develop training for spotting phishing attempts, using multifactor authentication to protect systems and explaining how brand trust and data protection are connected and a responsibility for all employees.
When marketers understand the value and risk of the data they touch every day, cybersecurity becomes less about following rules (no passwords written on a Post-It note) and more about protecting the company and ensuring growth.
For CMOs, building that fluency can also come from taking these actions:
- Join conferences and conversations. Cybersecurity conferences are not just for technical staff and executives. Pulse Conferences is bringing together CMOs and CISOs on the first day of RSAC, with “Trust at the Table: Balancing Innovation & Resilience,” a lunch event that reflects the understanding that marketing and IT need to work hand-in-hand on cybersecurity management to build trust and improve both internal and external communications. Other conferences like CyberMarketingCon in November, further support the shift toward more marketing and business-focused cybersecurity speakers, sessions and content.
- Track trust as an asset. Cybersecurity is often only spoken on in technical terms, with “Hackers used exploit XYZ to enter…,” but CMOs can bring a different perspective and analysis and set up trust-related indicators along with other brand metrics. The marketing team can, for example, examine customer churn after an incident or changes in surveyed brand sentiment after a misinformation campaign or deepfake scam. It’s important for CMOs to develop these types of metrics to better relate incidents to downstream shifts in brand loyalty, trust and engagement.
In 2026, CMOs don’t need to become cybersecurity experts who can name the latest malware and know all of the “patch days” by heart. Cybersecurity incidents will continue to happen, and customers will continue to judge companies by how they reacted, if they told the truth and if they helped protect the customer and their data going forward.
When cybersecurity is intertwined with brand value and growth, it’s no longer running in the background, it’s a core part of how brands build trust.
Key takeaways:
- Cybersecurity is now a brand and growth issue, not just an IT one
- AI-driven impersonation and misinformation are eroding trust at scale
- Resilience and recovery matter more than perfect prevention
- CMOs and CISOs must align to protect brand equity
Crisis-Proof PR: Telling the Story Before the Cybersecurity Breach

Cybersecurity breaches rarely fail because of problems with the related technology. They fail because teams aren’t aligned when breaches happen. Communications, legal and the C-suite might have different priorities and opinions about what should be said, to whom and how often. This disconnect can create tension, which builds to indecision and lack of transparency and action, which starts eroding reputational trust.
When a breach and crisis occurs, the instinct is often to move very fast. Speed feels like control. But without alignment, speed doesn’t create clarity; it creates confusion.
Alignment happens before the breach
Alignment doesn’t come from a single meeting or a shared document; it comes from decisions that are made proactively and reinforced over time through training and policy, including:
- Set decision ownership to establish who has final authority on external communications during an incident and if that authority/responsibility shifts as conditions change and more information becomes available.
- Define disclosure rules by setting what triggers customer, partner or public disclosure. What needs to occur before the communications plan is set in motion.
- Run tabletop exercises of breach simulations with multiple teams, including marketing and communications, legal, executive teams and their communications. This helps give everyone a practice run and gives the participants a chance to work out differences of opinion in private, so they don’t play out during a crisis.
- Establish escalation paths to ensure teams know how to quickly raise concerns or conflicting viewpoints without slowing the response or creating internal bottlenecks.
Alignment beats speed
During an active cybersecurity incident, competing priorities surface immediately. Cybersecurity teams focus on accuracy, containment and not sending premature disclosures about the depth of the breach, what it contained, who took it and a myriad of other details. The legal team is concerned about liability, class-action suits and trying to minimize regulatory trouble. And the executive team is thinking about lost revenue, the company’s reputation and the board members.
Each of these groups has valid reasons for their concerns and focus. The problems come when these differing priorities crash into each other during a live cybersecurity incident. The worst track to take? Paying hackers and pushing the incident under the rug. Several companies over the years have paid hackers to restore data or prevent further breaches, but they didn’t properly report the incident to regulatory authorities or customers. The results aren’t pretty when word gets out, both in terms of massive fines and a crippling blow to brand trust.
Who says what?
The disconnects and different priorities of these groups are why CEOs, CISOs and communications leaders need shared expectations in advance. They need meetings to discuss different scenarios and to establish:
- Who speaks publicly? Decide in advance who speaks, and if they cover the entire incident, or if a combination of speakers makes more sense. What circumstances would mean different executives need to come forward to speak. Maybe the CISO explains the incident first, detailing what exactly happened and what was accessed, stolen or disrupted, and later the CEO talks about trust, accountability and moving forward.
- What language is off limits? Choose what team members should set the communications guidelines that can prevent mixed messages, off-the-cuff comments or well-intentioned leaders contradicting one another during the most scrutinized moments.
- What messaging and tone is front and center? Teams should discuss how to explain uncertainty (about how a breach happened, what was exposed, etc.) without sounding evasive or shifting blame. Communications professionals can help guide this messaging to ensure it does not sound tone deaf, but focuses on plain language and directness.
When the next incident happens, the technical response will always matter to prevent hackers from going deeper or into other systems. But the narrative response is what shapes how customers, regulators and employees remember the incident and the company’s response. Organizations that invest in alignment before a breach don’t just respond faster, they respond with credibility.
Key takeaways:
- Cybersecurity crises fail due to misalignment, not technology
- Speed without alignment increases confusion and reputational risk
- Clear ownership and disclosure rules must be set in advance
- The breach narrative often matters as much as the breach itself